Category: Mobile Devices

Lenovo messed up big with Superfish on laptops, but the Yoga 2 tablet has another problem
A few weeks ago I bricked the tablet I was given by a good friend. It’s recoverable and not forever lost, but I calculated the amount of time spent restoring through ADB (or moving to Cyanogen) is far more than the value of the tablet. The amount of time to do this also makes it less expensive to just buy a new tablet, one with specs I want.
Since this previous tablet was a gift, I did some homework and because of my day job I had a good idea of what I wanted in a tablet. I also have been recommending Thinkpads for the last 8 years. So why not try a Lenovo tablet? The Yoga 2 covered all my needs, came in a decent 8″ size and boasted great battery life.
What the tablet website, all the reviews, and Lenovo itself failed to mention were two major problems:
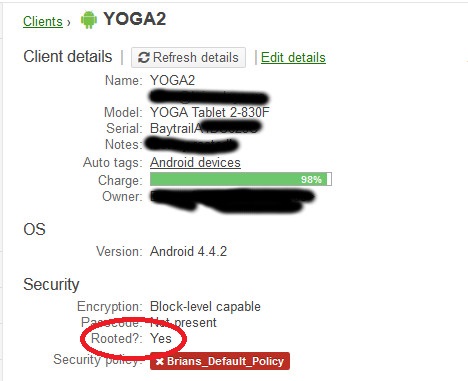
1. Lenovo Yoga 2’s have previously been rooted according to Cisco Meraki (or likely any other MDM)
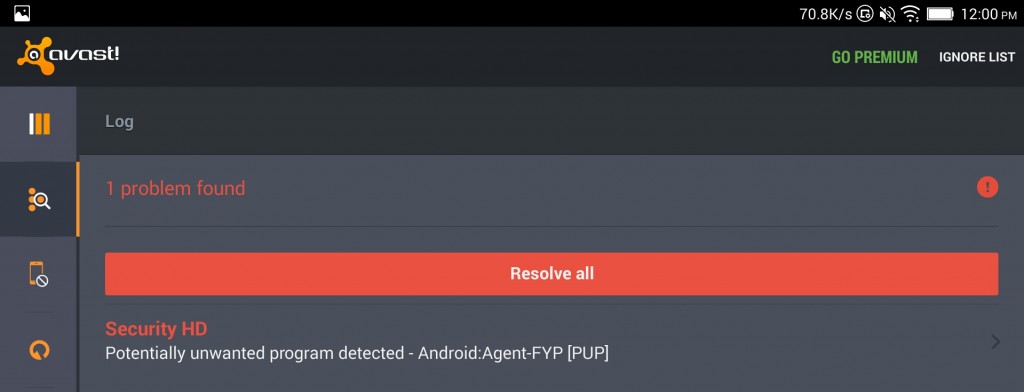
2. Lenovo Yoga 2’s come pre-loaded with junky malware called Security HD
So this isn’t as bad as Superfish, and I don’t want to give the impression that it’s on that level. It is however particularly disheartening to see there are problems with Lenovo’s tablets as well as the laptops.
It took a little searching to figure out that Security  HD is really just a re-branded and translated version of some existing Lenovo software called SECUREit.
HD is really just a re-branded and translated version of some existing Lenovo software called SECUREit.
Before someone can even click the I accept button to use Security HD, they are prompted to read the Security User Experience Improvement Program document (click link for a PDF print of this page). This page leads straight to an English generic terms of use for what Security HD/SECUREit can do. (On a side note the server running this page is outdated and vulnerable to several security flaws.)
Reading through the SECUREit page, it’s pretty clear that the only way to obtain the features it touts is to place it’s processes directly between the Internet and other apps on a device.
And it’s fairly likely the only way to place an app like this between other apps and the Internet is to develop the proper hooks into the base Android OS, or to root the OS, modify the system to allow this app to work, and then remove evidence to try and “un-root” the device. This sounds like exactly the sort of hack I would do if I wanted to unscrupulously intercept and monitor the traffic on someone’s tablet. Security HD of course is tagged as a system app and can’t be uninstalled without rooting the tablet.
It’s unfortunate that it came pre-shipped with this problem on it. I thought perhaps I was just the unlucky recipient of a jacked tablet. I called Lenovo tech support and tried to get an answer as to why my new tablet was detected as rooted. They didn’t have much of an answer of course, I never got beyond Level-1 tech support.
I knew I was expecting much considering they don’t even know how to operate their phone system. I was transferred at least three times, but I will have to go back and check the total number of times. After close to two hours I was kindly offered to be transferred to Android premium support for the lost cost of $39 per call. I demanded to not be charged, asked for a manager, all of that good stuff.
After not getting anywhere with that line of calling, and never really getting a straight answer, I called to get the unit replaced stating there is a problem with the software. This was the easiest imaginable transaction I had. With my existing case # I was able to get a new tablet shipped to me without question. Lenovo warranty support seems to have a lot of practice returning products.
This time I recorded my opening of the tablet from the packaging, all the way through until Meraki detected the tablet as rooted. I have to spend some time editing my personal info & login out of the video, so that will be awhile before it is posted. This brand new tablet detected as rooted immediately, and Avast again detects Security HD as malware.
I never trusted the original tablet to continue using it for long, but I used this new one to see what else I could find out before trying to return it as well. Turns out that even disabling Security HD is pointless, as it re-enables itself and runs whenever the tablet is restarted.
I would love to have the time to load Fiddler and see what kinda of insidious activity a Yoga 2 is really doing without the knowledge of its owner. But I don’t have that kind of time. The amount of time I have now spent chasing down Lenovo’s insulting behavior is more than enough to have brought my old tablet back to life.
For what it is worth, I will never again recommend a Lenovo to anyone again. I doubt I have found anything as significant as Superfish, and I know I haven’t investigated this as thoroughly as possible. But between Superfish and Security HD I am reminded that Lenovo is a company at the mercy of the Chinese government, and simply can’t be trusted. This is the same reason I will never purchase or recommend a Huawei or ZTE device either. To all my friends looking to buy a tablet or a new computer, I hear Dell is trying to make a comeback.
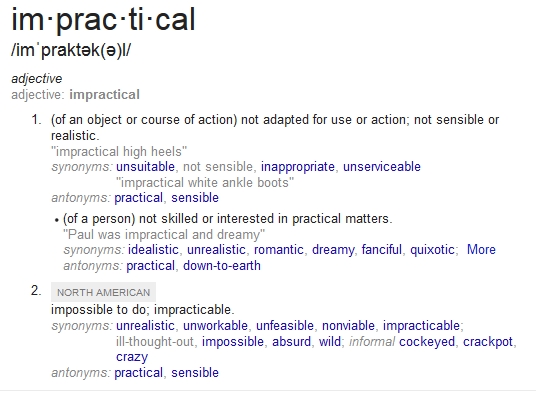
BYOD makes your organization less secure because it is impractical

BYOD which stands for Bring Your Own Device is a common topic lately amongst the IT Crowd. It’s one particular method for dealing with the escalating interest of employees wanting to do more work from tablets or smartphones. The strategy is as straight forward as it gets, let the employees bring whatever device they choose to work on, and the IT department will decide what and how the employee can or can’t do that work. While great on paper, the practical reality of a BYOD strategy is what makes it so ineffective.
If you’re still reading this, I’m going to assume you have an interest in IT, and particular the future of mobile technology in the workplace. It’s likely you have read articles, watched Gartner webcasts, and possibly even participated to some extent in a BYOD scenario. It’s also very possible you are reading the above and thought to yourself “Whoa! What the heck are you talking about, BYOD is a bad idea?”
BYOD on paper is a great idea, but it’s impractical to think it will simultaneously meet all of an IT departments security needs and the productivity desires of employees. The technology used for BYOD, known as a “secure container” is a special app or space on a device where all the company apps are stored in. The container is easily thought of as a locked box inside your device, where the IT department squirrels away the company data. Unfortunately the container really isn’t where most of your employees are going to do their work.
The concept of BYOD is impractical because it derives from the belief that staff members will only do their work in the way that an IT department believes staff should do their work. BYOD revolves around how an organization can predict or worse dictate how their staff will utilize a mobile device to accomplish their work. A BYOD strategy is incapable of acknowledging all the faster, easier, and sexier ways employees can and will get this work done outside the container. Because of this impractical expectation, BYOD programs are less secure than the IT staff behind them intend.
BYOD exists as a reaction from the world of IT Security and other IT groups over their ever burgeoning workload. They have allowed themselves to be distracted by the belief that work functions will be safe and secure if it is only accessed through this container. This is impractical and counter-productive on a device that is designed to allow people freedom to work however they want.

It’s impractical to believe this container is going to provide all the technology necessary for employees to fully realize the capabilities mobility can bring them. The container doesn’t matter when your business counts on enabling the versatility of your employees. When an employee is at an important event, they don’t have time to enter the container every time they need to take a note or a picture. They will use whatever app they are used to, and they will “copy that to the container later.” The container has not prevented data leakage.
When was the last time you emailed something to your work address from your personal address? It’s a very easy thing to do. It doesn’t matter if staff sign an agreement, once the data is outside the container, it is outside the control of IT. The harder it is for someone to use their mobile device to perform work functions, the more encouraged they may be to find a way around your controls. Is it easier to work on your full-featured document editing app that came with the tablet, or the restricted editor in the container? People send documents through Dropbox or their Google Drive all the time because it is easier and often faster than using the mechanisms provided by their company. It really doesn’t matter how great your written policy is, people will work how they want to work. Shadow IT is a term today because IT departments are spending too much time restricting the tools people want to use to be more productive.
Because BYOD is impractical and drives your staff further away from playing by the rules, the alternative of company-provided equipment is the only way to securely enable mobility for your people. If you are asking your staff to work on a device, give them a secure device that does its best to stay out of the way of the person using it. To provide a secure device that provides as much capability as possible is a difficult recipe to get correct, and any IT department is going to approach these devices in a new, but similar fashion to traditional endpoints like desktops and laptops.
The alternative to BYOD, that of corporate-owned devices is a follow-on topic to this. Look for that shortly!