Last month my perspective on safe computing and what that really means; not only to me personally, but also as an IT administrator changed. Reinforced may actually be a more accurate word. For months and apparently years the (insert company name) has been operating under the guise of “we’ve been safe so far, so why change things?” This approach towards server and network security has resulted in a really embarrasing lack of safe computing, and really seems to be a less responsible approach than what many were charged with accomplishing.
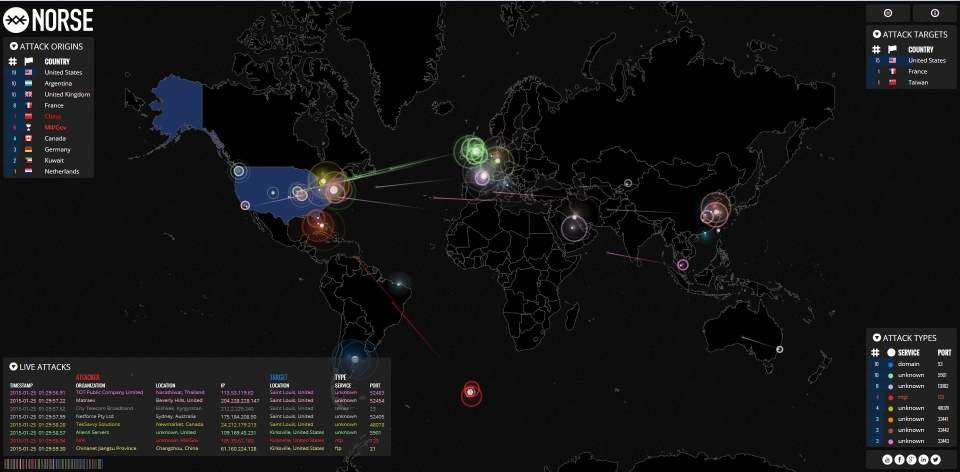
In short we were hacked. I wish I could say I was thankful that it was this group over that one, but in the end we were hacked. After this incident hack doesn’t appeal to me as a verb to describe the malicious, intentioned, educated and well organized attack against the IT network. I wish I could say I am thankful that it didn’t go completely undetected, that I am thankful it didn’t result in severe data-loss, and that I’m thankful for the responsiveness and dedication by the IT staff to mitigate the ensuing chaos.
Unfortunately the following is a non-exhaustive list of failures within the organization for our security:
- Lack of perimeter security
- Lack of two-factor authentication
- Lack of centrally managed and monitored antivirus software
- Lack of secured firewalls on servers
- Lack of notification from security department that there was a breach
All of these resulted from irresponsibility on many different groups. No single entity can be blamed, and no single entity can be thanked for minimizing the impact the incident could have had. Sensitive data *could* have been compromised, and that is a failure in foresight.
After I stopped playing the security hat 10 years ago I moved forward with my career and worked on administration and management of progressively larger data networks. At no time did I ever convince myself my network was secure. But then again I’m very paranoid about that. To trounce around with a public IP address sitting on the internet with no IPSec policy and no firewall is inviting the worst. I claim no superiority from one OS to the other, that is irresponsible.
My focus on security has instantly been revitalized. In addition to that a recognition of how basic security works has become prominent once again. The only secure computer is one that is turned-off, unplugged from the wall, and stored in a vault. This computer will never again be powered on, and that is only a good start. With the ability to freeze memory chips with their electronic registers still full, no computer is or ever will be safe.
But I still bank online.
There is a need for security at the corporate level that will go beyond the need for personal security on a home PC. But the basics still apply.
Have a firewall and Keep your a/v software up to date. Not terribly difficult.
As computers and the networks that connect them become increasingly complex and their scale increases, so to does the complexity and scale of effort needed to properly manage them. The days of building servers from a disc, installing an application and walking away are sadly gone. Sadly as well the days of no-accountability are gone with them. Within the last decade revolutionary changes have transformed every IT shop from a place to hang-out, drink beer, and play video games, to a place where companies increasingly rely on the functionality provide by the services IT provides.
Do you think it is acceptable to go 24 hours without email service anymore? How about 48 hours? One week?
How do you feel about electricity? The same evolution of automobiles, electricity, the telephone, and flight from luxury to utility has encroached on the “IT is fun” mentatlity that not so long ago was status-quo. IT is now business.
And like a brick-and-mortar business, someone breaking in results in a few expected behaviors. The authorities may or may not be called, but locks will probably be replaced, and possibly cameras added. Not much can prevent someone deteremined enough from breaking in. Whether someone’s determination is exposed through physical or digital means has less effect on the desired outcome than one would like.
So what is the strongest defense? It is true that you can only build a wall that is high enough to keep people out, until someone comes along and builds a taller ladder. Computer security can only be as rigid and secure as that wall. No network is impenetrable. Last month I was reading an article from Popular Science about Chinese hacking groups that have near-free reign to exploit the security of global systems. The article doesn’t provide direct linkage to support from the Chinese government, but the author is sure of this.